Attempts to intercept hack or eavesdrop could be occurring at any point so all network traffic is encrypted to reduce these risks. Zero trust network access ZTNA also known as software-defined perimeter SDP solutions are designed to implement and enforce an organizations zero trust policy.
 Zero Trust Security Model Alexander S Blog
Zero Trust Security Model Alexander S Blog
This ZTNA policy is also applied when users are on the network which provides the same zero-trust approach no matter where a user is connecting.
Zero trust network. Since zero trust is an iterative process inspecting and logging all traffic will provide valuable insights into how to improve the network over time. Zero-trust networking is becoming more sought-after among companies fearing a data breach. Be ready to handle attacks before they happen.
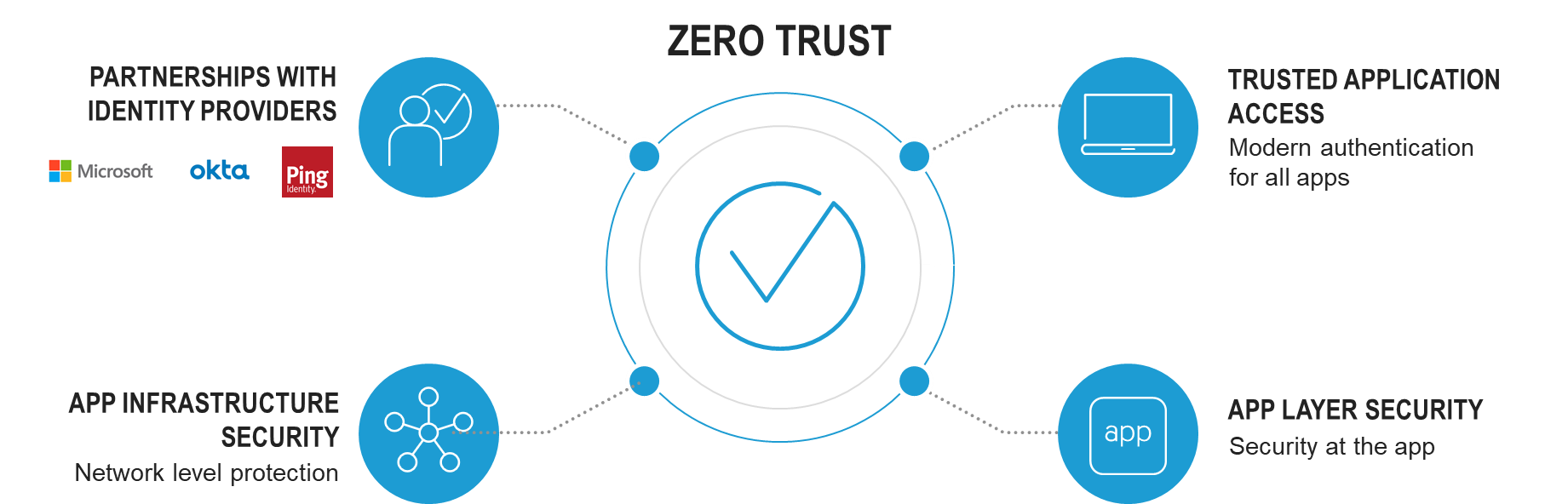
Zero-trust network access ZTNA connections grant access on a per-session basis to individual applications only after devices and users are verified. Additional considerations and best practices. We can no longer assume that internal entities are trustworthy that they can be directly managed to reduce security risk or that checking them one time is enough.
Zero Trust Network Security. The Zero Trust Network or Zero Trust Architecture model was created in 2010 by John Kindervag who at the time was a principal analyst at Forrester. To make this happen we follow three Zero Trust principles.
Zero trust network access ZTNA also known as the software-defined perimeter SDP is a set of technologies that operates on an adaptive trust model where trust is never implicit and access is granted on a need-to-know least-privileged basis defined by granular policies. The applications are hidden from discovery and access is restricted via a trust broker to a set of named entities. Rooted in the principle of never trust always verify Zero Trust is designed to protect modern digital environments by leveraging network segmentation preventing lateral movement providing Layer 7 threat prevention and simplifying granular user-access control.
In the ecosystem of a Zero Trust network users and data traffic are assumed to be operating in an open and unsecured environment such as the public internet. A Zero Trust Network in Practice. Perimeter-based security architecture therefore the zero trust security architecture comes into being.
This talk explains why past solutions like SDN or SDF arent great and how HashiCorp Consul can help you build a zero-trust network that works for your engineering teams. Zero trust is a strategic approach to security that centers on the concept of eliminating trust from an organizations network architecture. The software-defined networking solution focuses on providing connectivity between heterogeneous environments cloud to data center application.
Users attempting to connect to an organizations applications are only permitted to do so if. In the Zero Trust model there are three key objectives when it comes to securing your networks. Trust is neither binary nor permanent.
Microsoft has a long history of working with customers on how to protect against a broad range of security attacks and we are one of the largest producers of threat intelligence built on the variety of data that flows through our network. Minimize the extent of the damage and how fast it spreads. The zero trust security architecture establishes a dynamic digital identity-based perimeter with four key capabilities which are identity-based schema resource secure access continuous trust evaluation and adaptive access control.
Taking a Zero Trust approach can help to ensure optimal security without compromising end user application experiences. Because human error accounts for approximately 90 of breaches you should focus your security efforts on keeping people. Zero Trust Network is an application and identity-centric connectivity solution designed for cloud-to-on-premise and multi-cloud networking.
Zero trust network access ZTNA is a product or service that creates an identity- and context-based logical access boundary around an application or set of applications. Increase the difficulty of compromising your cloud footprint. The zero trust model of network security relies on the verification of user identities before allowing them onto your companys network.
A Zero Trust network treats all traffic as untrusted restricting access to secure business data and sensitive resources as much as possible to reduce the risk and mitigate the damage of breaches.
