The increased reliance on cloud computing has created the perfect environment for cybercriminals to take advantage of unprepared companies. How should cyber security be in a cloud service.
 Eyes On The Prize The Internet Of Things Cyber Security Cloud Computing
Eyes On The Prize The Internet Of Things Cyber Security Cloud Computing
Ad Explore new cybersecurity trends technologies and approaches.

Cybersecurity in cloud computing. Cybersecurity deals with the protection of computer systems and data stored in it. Ad Explore new cybersecurity trends technologies and approaches. As data continues to move to the cloud many cyber security professionals are struggling to maintain the security of their cloud environments.
Strengthen and Streamline Cybersecurity Across Multiplatform Environments. When using cloud services be it software-as-a-service SaaS or infrastructure-as-a-service IaaS the customer always has some level of responsibility for. Knowledge gained in cloud computing will act as a driving force and an added advantage for those opting for a career in Cyber Security.
Cloud computing is opening up new challenges. Learn more about how to secure your data here. Together we can make networks devices and applications more secure.
Cybersecurity in Cloud Computing Use a Password Manager. According to the National Cyber Security Alliance over 70 percent of small businesses were attacked and many of them do not bounce back. Strengthen and Streamline Cybersecurity Across Multiplatform Environments.
This article discusses the importance of implementing cybersecurity measures the limitations of cloud computing and tips on how to apply security protocols. One of the challenges in a company is having too many accounts. The cloud computing security is that the blend of the technologies and tips that the management is dependent upon basically portrays overseeing the consistency leads and secure infrastructure data applications safe-secure directions framework and information applications relates identifies to cloud computing use.
Further employees tend to make weak passwords like 123456 Or they tend to make really strong ones that are hard to remember. Together we can make networks devices and applications more secure. Constraints with Cloud Computing The benefits of using an IaaS provider are obvious no need to spend money on buying and maintaining expensive servers and computing power along with a general sense that your data is.
The access to the web or application must be endowed with an SLL Secure Sockets. Also lots of tools mean lots of passwords. Ad Microsoft Security Provides Integrated Security with Full Coverage.
So how can you solve this issue. In general data infringement happens when cyber-criminals target an organization that can access the cloud network without authorization or use programs to download copy and transfer data. Threats Infringements of records The problem of leaks or data loss because of data breaches the most prevalent threat to cloud storage.
Ad Microsoft Security Provides Integrated Security with Full Coverage. Cloud services must comply with cyber security standards that guarantee the integrity of the data of the users and companies that contract the services. To begin with cloud computing must offer secure navigation.
 Cloud Computing Trends Cybersecurity Leads Twitter Mentions In Q4 2020
Cloud Computing Trends Cybersecurity Leads Twitter Mentions In Q4 2020
 Cloud Cybersecurity Untuk Infrastruktur Kritis Nasional Cloud Computing Indonesia
Cloud Cybersecurity Untuk Infrastruktur Kritis Nasional Cloud Computing Indonesia
 7 Key Cybersecurity Threats To Cloud Computing Cloud Academy
7 Key Cybersecurity Threats To Cloud Computing Cloud Academy
 Cybersecurity Issues In Cloud Computing Need To Be Addressed Verdict
Cybersecurity Issues In Cloud Computing Need To Be Addressed Verdict
 Cloud Cyber Security For National Critical Infrastructure
Cloud Cyber Security For National Critical Infrastructure
 Cyber Security In Cloud Computing Attackers Threats
Cyber Security In Cloud Computing Attackers Threats
 Cyber Security Cloud Computing Iot And Data Science Are The Next Booming Sectors Express Computer
Cyber Security Cloud Computing Iot And Data Science Are The Next Booming Sectors Express Computer
 Protecting Data Via Cloud Computing Pymnts Com
Protecting Data Via Cloud Computing Pymnts Com
 Why The Future Of Cybersecurity Is In The Cloud Cloud Computing News
Why The Future Of Cybersecurity Is In The Cloud Cloud Computing News
 Green Cloud Computing For Cybersecurity Download Scientific Diagram
Green Cloud Computing For Cybersecurity Download Scientific Diagram
 Cybersecurity With Cloud Computing 2015
Cybersecurity With Cloud Computing 2015
 The Overlapping Realities Of Cyber Security And Cloud Computing Manipal Prolean
The Overlapping Realities Of Cyber Security And Cloud Computing Manipal Prolean
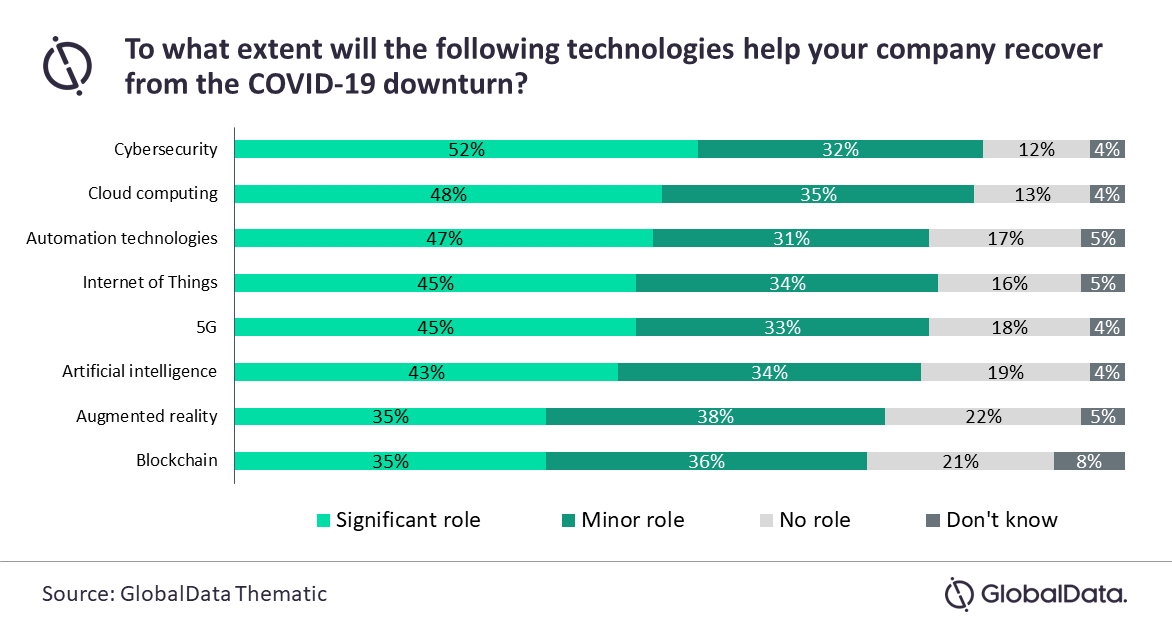 Businesses Turn To Cybersecurity And Cloud Computing To Overcome Covid 19 Challenges Globaldata
Businesses Turn To Cybersecurity And Cloud Computing To Overcome Covid 19 Challenges Globaldata
 How To Approach Cloud Computing And Cyber Security In 2018 T Dg Blog Digital Thoughts
How To Approach Cloud Computing And Cyber Security In 2018 T Dg Blog Digital Thoughts

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.